Integrity Definition In Information Security
For more FREE IT Security training videos visit our sit. Security controls focused on integrity are designed to prevent data from being modified or misused by an unauthorized party.
 Information Security Risk Management Or Isrm Is The Process Of Managing Risks Associated With The Use Of Info Risk Management Security Information Technology
Information Security Risk Management Or Isrm Is The Process Of Managing Risks Associated With The Use Of Info Risk Management Security Information Technology
Data integrity maintenance is an information security requirement.

Integrity definition in information security. Ideally only authorized users modify data. An ISMS is part of a larger management system. To preserve the integrity of information means to protect the accuracy and completeness of information.
Untrusted data is devoid of integrity. Why is maintaining the integrity of. In the field of information security as well as in the fields of e-Business and computing it is of great importance to ensure the genuineness of physical or electronic documents communications transactions and data.
Data security refers to the protection of data while data integrity refers to the trustworthiness of data. In the world of information security integrity refers to the accuracy and completeness of data. This type of protection is most important in military and government organizations that need to keep plans and capabilities secret from enemies.
Integrity provides assurances that data has not changed. Integrity assures that the data or information system can be trusted. Confidentiality is the protection of information in the system so that an unauthorized person cannot access it.
Integrity is a major IA component because users must be able to trust information. Integrity involves maintaining the consistency and trustworthiness of data over its entire life cycle. An information security policy statement expresses managements commitment to the implementation maintenance and improvement of its information security management system.
User Ids and passwords access control lists ACL and policy based security are some of the methods through which confidentiality is achieved. Integrity is the protection of system data from international or accidental unauthorized changes. Heres a broad look at the policies principles and people used to protect data.
The CIA Confidentiality Integrity Availability triad is a widely used information security model that can guide an organizations efforts and policies aimed at keeping its data secure. The other four are authentication availability confidentiality and nonrepudiation. Although the security program cannot improve the accuracy of the data that is put into the system by users.
The challenges of the security program are to ensure that data is maintained in the state that is expected by the users. Control their information security risks. The integrity standard of the technical safeguard requirement dictates that entities implement policies and procedures to protect ePHI from improper alteration or destruction.
Maintaining the integrity of ePHI is a primary goal of the Security Rule. Data security focuses on how to minimize the risk of leaking intellectual property business documents healthcare data emails trade secrets and more. Authenticity is an integral component of information security.
Information security is a set of practices intended to keep data secure from unauthorized access or alterations. In this context confidentiality is a set of rules that limits access to information integrity is the assurance that the information is trustworthy and accurate and availability is a guarantee of reliable access to the information by authorized people. However there are times when unauthorized or unintended changes occur.
Integrity is one of the five pillars of Information Assurance IA. This includes ensuring that no one has modified tampered with or corrupted the data.
The Cia Triad Confidentiality Integrity Availability Panmore Institute
 Storytelling Agency Studio 7c Integrity Quotes Value Quotes Quotes To Live By
Storytelling Agency Studio 7c Integrity Quotes Value Quotes Quotes To Live By
 Statistics Infographic Infographic 6 Cyber Security Statistics You Should Know Infographicnow Com Your Number One Source For Daily Infographics Visual Cybersecurity Infographic Cyber Security Awareness Cyber Security Education
Statistics Infographic Infographic 6 Cyber Security Statistics You Should Know Infographicnow Com Your Number One Source For Daily Infographics Visual Cybersecurity Infographic Cyber Security Awareness Cyber Security Education
 Itil Information Security Management Risk Analysis Internal Audit Management
Itil Information Security Management Risk Analysis Internal Audit Management
 Data Integrity Infographic Data Integrity Data Integrity
Data Integrity Infographic Data Integrity Data Integrity
 Essential Terminology In Cyber Security Info Savvy Cyber Security Cyber Security Technology Cyber
Essential Terminology In Cyber Security Info Savvy Cyber Security Cyber Security Technology Cyber
 What Is Cyber Security A Thorough Definition Cyber Security Protected Health Information Cybersecurity Framework
What Is Cyber Security A Thorough Definition Cyber Security Protected Health Information Cybersecurity Framework
 My Life Is Built Around Acting With Moral Integrity And Values Every Single Day Of My Life Integrity Quotes Quotations Wise Words
My Life Is Built Around Acting With Moral Integrity And Values Every Single Day Of My Life Integrity Quotes Quotations Wise Words
 Need Some Random Knowledge There S A Chart For That 28 Photos Cyber Security What Is Cyber Security Security Tips
Need Some Random Knowledge There S A Chart For That 28 Photos Cyber Security What Is Cyber Security Security Tips
 Cia Triad Security Priorities Cyber Security Priorities Security
Cia Triad Security Priorities Cyber Security Priorities Security
 Pin On Security Privacy Tutorials
Pin On Security Privacy Tutorials
 Venn Diagram Infosec Principles Confidentiality Integrity And Availability Assessment Checklist Cyber Security Security Tips
Venn Diagram Infosec Principles Confidentiality Integrity And Availability Assessment Checklist Cyber Security Security Tips
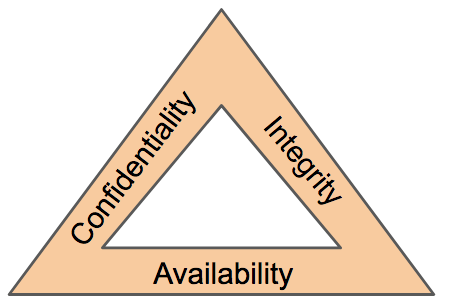 Confidentiality Integrity And Availability The Cia Triad Certmike
Confidentiality Integrity And Availability The Cia Triad Certmike
 Data Governance Best Practices For Collection And Management Of Data With Data Governance Tools Master Data Management Data Best Practice
Data Governance Best Practices For Collection And Management Of Data With Data Governance Tools Master Data Management Data Best Practice
 5 Steps In Building A Successful Data Governance Strategy In 2021 Reviews Features Pricing Comparison Pat Research B2b Reviews Buying Guides Best Pra Data Project Management Tools Strategies
5 Steps In Building A Successful Data Governance Strategy In 2021 Reviews Features Pricing Comparison Pat Research B2b Reviews Buying Guides Best Pra Data Project Management Tools Strategies
 What Is The Cia Security Triad Confidentiality Integrity Availability Explained Bmc Software Blogs
What Is The Cia Security Triad Confidentiality Integrity Availability Explained Bmc Software Blogs
 What Is A Pii Breach Free Cyber Security Awareness Poster Cyber Security Awareness Awareness Poster Cyber Security
What Is A Pii Breach Free Cyber Security Awareness Poster Cyber Security Awareness Awareness Poster Cyber Security
 Isms Iso 27001 Certification Urs Management System Security
Isms Iso 27001 Certification Urs Management System Security
 Security Governance Services Maryland Security Solutions Security Computer Security
Security Governance Services Maryland Security Solutions Security Computer Security
Post a Comment for "Integrity Definition In Information Security"